The NeuroSolutions subdomain for Massachusetts Institute of Technology (MIT) has been defaced by a hacker going by the alias of Trenggalek G3tar a.k.a Trenggalek 6etar. The hacker posted a simple message, simply stating:
hacked by Trenggalek g3tar
The defacement itself may seem simple, however, the level of severity and impact is massive. Hacking one of the most prestigious technology-based institutions in history is a great feat to accomplish and should not be taken lightly. The hacker seems to have taken advantage of the recently addressed WordPress REST API bug, editing the websites thread posts, defacing the page. Recently, the bug has allowed hackers to hack not just MIT, but other high priority organizations, institutions and governmental agencies too.
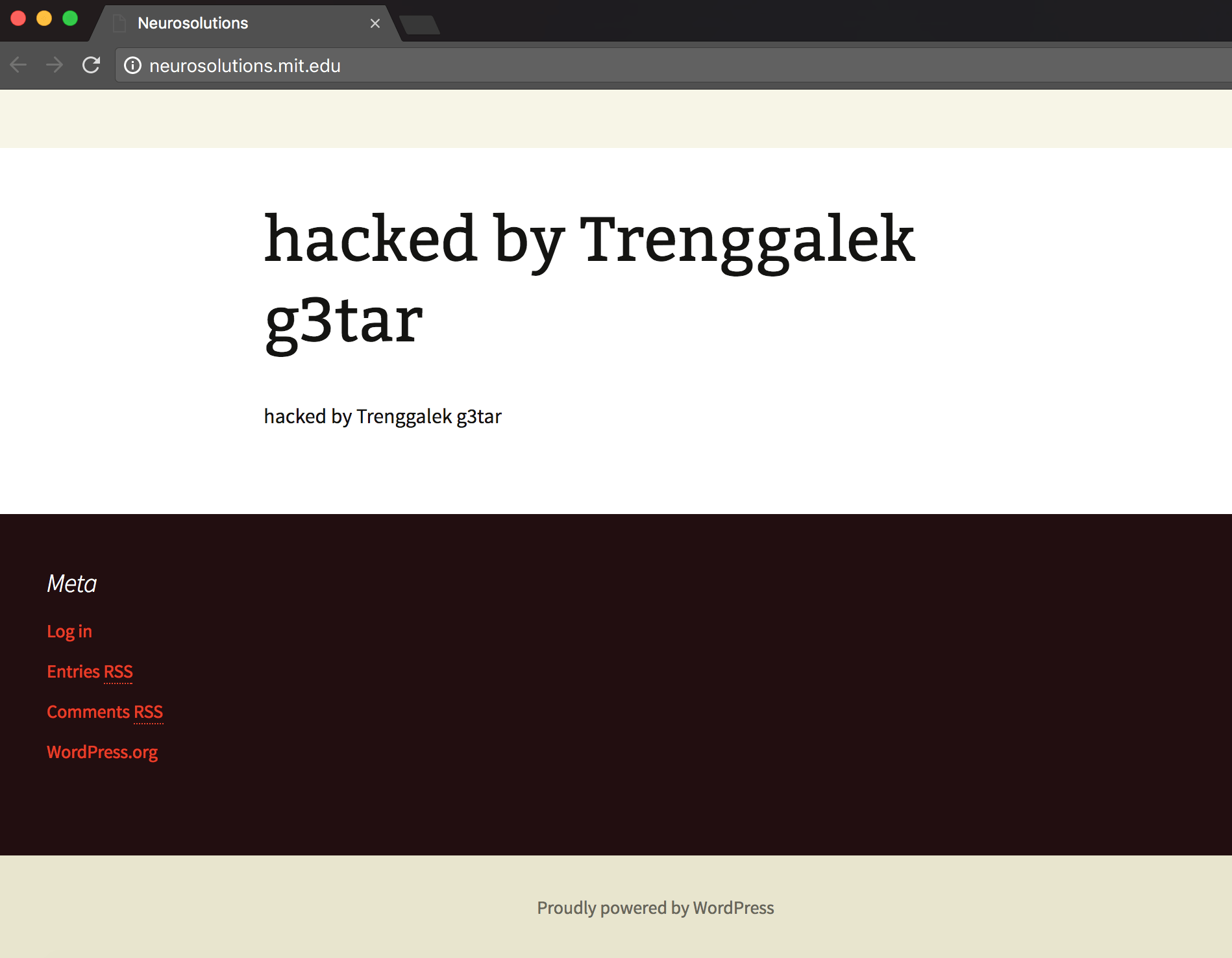
The system administrators at MIT have yet to notice the defacement because the webpage is still defaced as of the writing of this article. We have contacted the IT staff over at MIT to address the breach, however, we have not received a response as of yet. Hopefully, our message reaches them so they notice the attack and restore the defacement as soon as possible.
The bug from WordPress has proved to be costly, however, it proves to show how dangerous a 0day exploit can be, especially when millions upon millions of clients and users use the same CMS the vulnerability exists in. The hack and defacement of the NeuroSolutions subdirectory of MIT may seem insignificant, however, this is due to the fact that hackers such as Trenggalek G3tar only deface these high priority websites for the sake of enhancing the list of websites they have stamped their names with. Black hat hackers could be much more malicious and destructive using the same methods by uploading viruses, affecting all users who use the attacked website or by social engineering and phishing users for their private details.