Securing data interactions is one of the most critical factors in the cybersecurity space and network security space. A recent tweet on data security during the US elections concluded that IT network security is not just limited to enterprises but has a broad spectrum of applications.
For larger enterprises having employees scattered across the globe, network security becomes paramount, especially in the current pandemic situation. Take an example of the software development company somewhere in Atlanta with employees, cyber assets, and vendors scattered across the US.
Without a reliable IT network security plan, the data exchange across multiple assets can be exposed to cyber-attacks. Here, we are exploring some essential aspects of building your business’s best IT network security plan.
Risk Management Framework
Any network security plan must include some of the most important foundational aspects that help mitigate risks and secure systems. They are,
Confidentiality: Non-disclosure of critical information to devices, users, and vendors without authorized access
Integrity: A property exhibited to ensure that there is no exposure to unauthorized data access or exchange
Non-Deniability: The exchange of information is mutual, where the receiver provides proof of receiving the data, and the sender will give an authorization id for delivering data.
Authentication: Validating and verification of identities for user acess, process, or device
Based on these fundamentals, the first thing an enterprise or a software development company can do is create an RMF or Risk Management Framework.
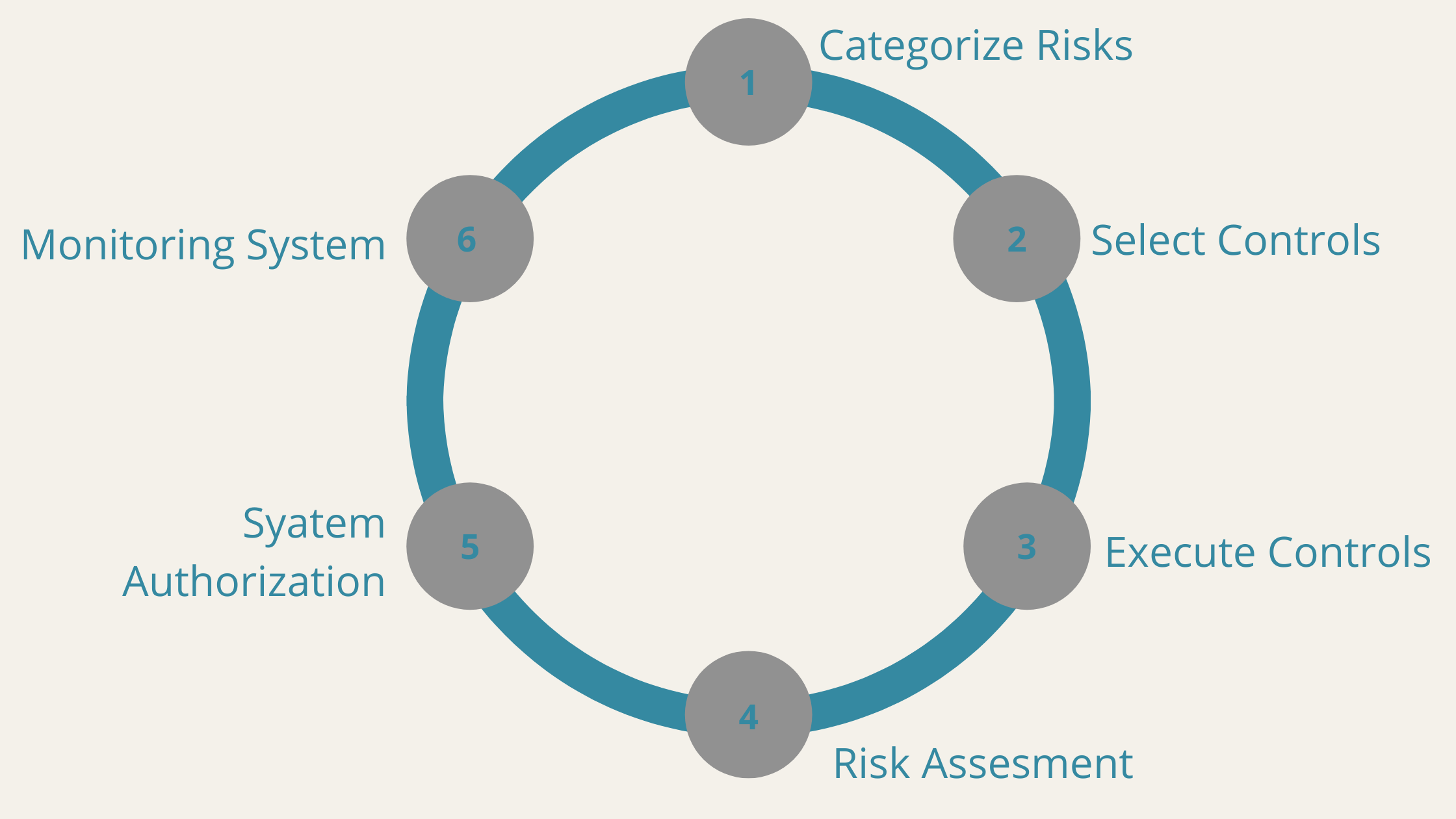
- Categorize the Risks: It is quintessential for any business to categorize the cyber risks before devising a framework. The cyber threats specifically for network security need categorizations on different levels like cloud, subnets, and others.
- Select Controls: Select security controls for your organization according to the type of risks; for example, think of cloud network security; you have a multi-cloud network for data exchange. There are many security risks. To mend such dangers, your organization can use Intrusion Detection Systems or IDS.
- Execute Controls: Execute the selected controls to have an initial drill for understanding the effectiveness of security.
- Risk Assessment: Once you execute the drill, assessing the security controls becomes easier, helping you understand the the controls, add extra tools, and authorize the system for a complete risk assessment.changes that are needed.
- System Authorizations: Recalibrate
- Monitoring the System: Monitor the authorized system to check on the risks, and deploy advanced technologies like Artificial Intelligence algorithms to predict unknown risks.
Once you have a risk management plan ready, it is time for your organization to define the system accordingly.
System Definition
Every organization employs different kinds of systems, and every single one of them does not require equal protection. Defining the system helps the identification of critical touchpoints and assess the risks. So, you can have better control of systems and protect them against cyberattacks.
Properly defined systems are essential to the precise identifications of vulnerability. Let’s take an example of the software development company in Atlanta with several physical and virtual systems. Here are the critical points of system definitions that can help create an IT network security plan.
- Identify the logical and physical boundaries of the system within the environment.
- Define the components and resources that belong to the system.
- Define the purpose and primary functions of a system.
- Define the architecture of the system and different data flows.
- Gather the details of different interfaces and protocols.
Now that you have an RMF and defined the system, the next step is to identify the cyber assets and classify them.
Asset Identification and Classification
Cyber assets are as important as your fixed assets in a bank locker! For any organization, different types of physical and virtual assets are at work. Identifying these assets and classifying them will help you assess their vulnerabilities.
So, how can one Define a Cybersecurity Asset?
There are different approaches to identifying cyber assets, but the most standard is the one defined by NERC(North American Electric Reliability Corporation). The non-profit organization provides a detailed guideline on how to determine your cybersecurity assets and classify them.
These assets include,
- Control panels
- Data acquisition systems
- Networking equipment
- Virtual machines(VMs) or storage space
- Alternate power supplies or other electronic equipment that support the system
Though the list of cybersecurity assets you can include does not limit only the ones discussed here and has a broader range. Now that you have identified the assets and classified them let’s understand how to secure them with Electronic Security Perimeter (ESP).
Electronic Security Perimeter
An ESP is like an interface or a guardian wall between the cyber assets and external network. It becomes a critical contact point between a network communication link and the access point. Let’s understand a few essential elements of the ESP to appreciate its architecture.
Electronic Access Controls:
It is an entity that executes and documents the organizational processes for technical procedural mechanisms that control electronic access at all critical points of an electronic security perimeter. So, you can say that these are the guards at different gates of ESP.
Electronic Access Monitor:
It is an entity in the ESP architecture responsible for monitoring and logging all the access activities. It monitors access to ESP by different network communication links. Any network communication is routed through different subnets, routers, and other access points monitored through ESP.
Now you know CCAs(Critical Cyber Assets) and created a perimeter for network communications. So, all you need is a system-wide cybersecurity policy to have homogenous secure operations.
Cyber Security Policy
Cybersecurity policies establish the rules for employees, consultants, partners, board members, and even users who access your apps online. Policies can even cover internet resources, data networks, and other CCAs.
The first part of your policy must cover responsibilities and roles. For example, a software development company should include a detailed description of functions, stakeholders, consultants, IT staff, and even the financial staff. A policy can also set standards for an organization’s activities like email attachment encryption and restrictions on social media platforms.
The policy should also include rules of engagement for employees that access the system. For example, every employee should encrypt personally identifiable information (PII) before accessing systems remotely.
Conclusion:
From risk management, identifying critical assets, and creating a cybersecurity policy, everything depends on execution. If you don’t have effective enforcement and monitoring strategy for cybersecurity policies, your systems may become vulnerable.
Any software development company in Atlanta can create a reliable IT network plan by following the steps we discussed here. Most importantly, their system security will comply with NERC guidelines. Companies can integrate innovations like Artificial Intelligence and Machine Learning algorithms for reliable IT network security as we move forward.