October 26, 2017. jQuery blog hacked. Not the first time the site has been hit, and it’s quite a relief that the library remains intact.
Just how vital is the library? As alarming as the most popular JavaScript library running on the world’s most popular CMS being hacked sounds, the incident could mean the compromise of millions of sites that use jQuery.
Their official WordPress blog (blog.jquery.com) was defaced with a post that read “S.O.A. was here!” followed by the hackers’ pseudonyms “str0ng & n3tr1x.” It appeared on the URL http://blog.jquery.com/2017/10/26/hacked/(now removed). A screenshot is the only remnant of the jQuery blog post published under jQuery core member Leah Silber’s name:
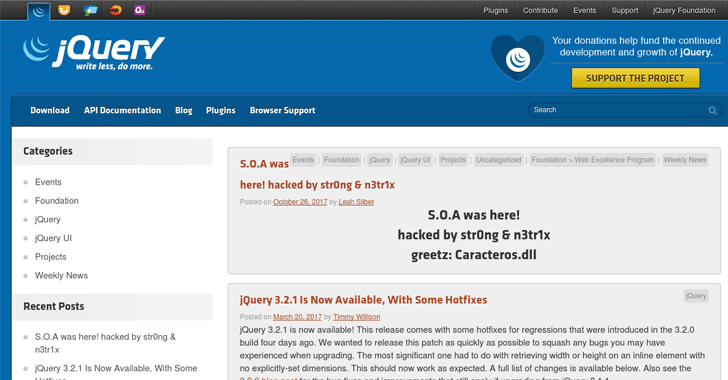
Perhaps the hackers merely reused a leaked password from a previous data breach or gained unauthorized access through exploiting a known or zero-day vulnerability, either from the WordPress script or the server itself.
The jQuery website was compromised with malware attacks twice in the same month of September during the year 2014, where guests were redirected to an RIG exploit kit. Like recent 2017 attack, library files were not affected or modified. Moreover, no evidence was found whether code.jquery.com server was compromised this time around.
Interestingly, mining service Coinhive was also hacked on October 23rd via their DNS provider Cloudfare. The modified version tricked millions of site visitors’ CPUs to mine cryptocurrencies to the hacker’s convenience. The browser-based cryptocurrency miner admittedly failed to create unique account passwords, nor even bother to change it for 3 long years.













