Zero-trust security architecture is a cybersecurity strategy that only permits authenticated users access to a company’s digital resources by default. User experience, network infrastructure, and cyber threat defense are all improved in a well-tuned zero trust architecture.
In this article, we’ll look at zero trust for the cloud, the role of zero trust, and the benefits of using it.
What Is Zero Trust?
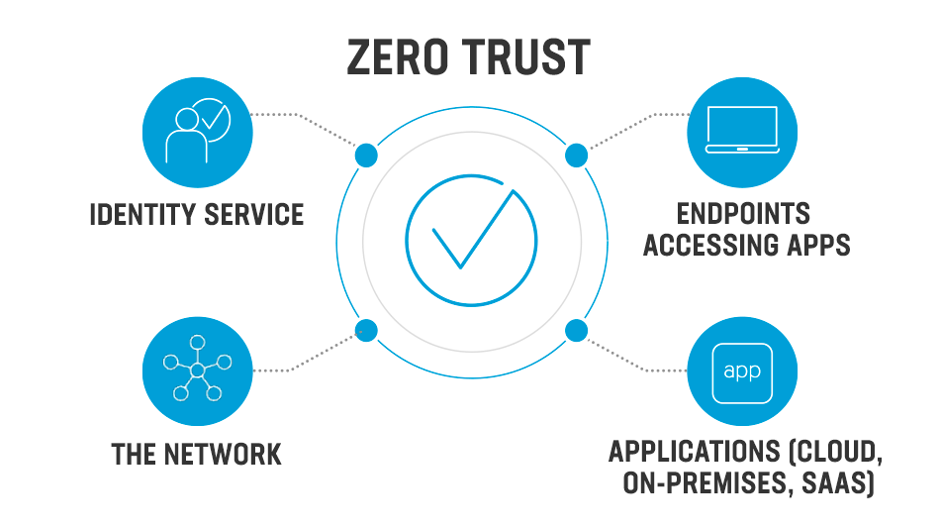
Zero trust is a cloud data security approach that does away with the concept of trust to secure networks, applications, and data. Contrary to the typical perimeter security approach, which operates under the premise that good users are always on the trusted side of the network and bad actors are always on the untrusted side, this is a glaring deviation from the norm. These presumptions are invalidated by zero trust, which assumes that all users are unreliable.
What Is Zero Trust Network Access?
Zero trust network access (ZTNA) offers secure remote access to programs and services, much like a virtual private network. However, a ZTNA, in contrast to a VPN, is based on set access control policies, limiting access by default and allowing users access to services only when specifically permitted.
Users are only able to see the applications and services they are authorized to access after ZTNA authenticates them through a secure, encrypted connection. This defense strategy stops lateral attacker movement, a flaw that hackers use to scan and switch to other services. In addition, organizations can use ZTNA to build location- and device-specific access control policies, limiting the ability of potentially hacked devices to connect to their services.
Why Should We Use a Zero Trust Model?
A business network’s implementation of zero trust depends on the company controlling the network. It establishes where limits can be created and sustains access constraints to protect critical applications, such as those in on-premises data centers, against unauthorized access and lateral movement.
The IT sector has always depended on perimeter security tactics to secure its most precious assets, including user data and intellectual property. These security measures included inspecting and verifying users entering and exiting the network using firewalls and other network-based tools. However, the adoption of hybrid cloud architectures and digital transformation is altering how various sectors conduct their operations. A network boundary is no longer sufficient for security.
Since users, resources, and data are dispersed across the world, connecting them swiftly and securely is challenging. Additionally, without a typical on-premises infrastructure to provide security, the working and personal surroundings of employees are more susceptible to intrusion, endangering the company.
Role of Zero Trust
Reduce the Risk of a Data Breach
Every entity is presumed to be hostile based on the concept of least privilege. Before providing permissions, each request is analyzed, people and devices are verified, and permissions are evaluated. An attacker who gains access to your network or cloud instance through a compromised device or other weakness won’t be able to access or steal your data if they don’t have the necessary permissions. Additionally, the zero trust design creates a secure area with no lateral movement options, leaving the attacker with nowhere to go.
Reduce Business Risk
Zero trust solutions prevent any apps or services from exchanging data until their identity attributes, which are immutable characteristics that comply with predetermined trust standards like authentication and authorization criteria, have been confirmed. Therefore, zero trust lowers risk since it clarifies what is on the network and how those assets interact.
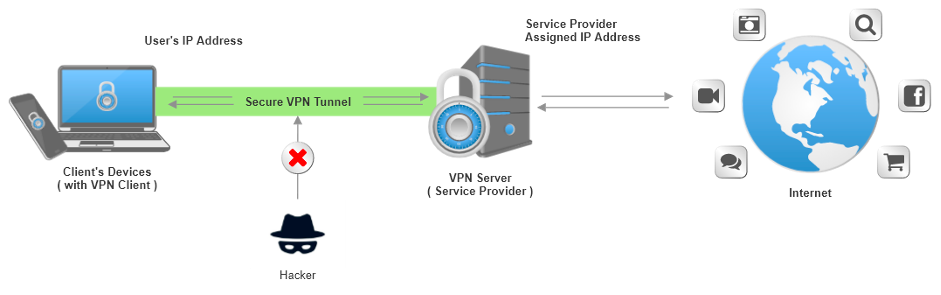
Replacing a VPN
Many businesses rely on VPNs to protect their data, but as was already mentioned, VPNs are frequently inadequate to protect against today’s threats. While VPNs cause delays and can reduce productivity for distant workers, Zero Trust can extend safe access control to connections made from any location.
Support Compliance Initiatives
By employing fine-grained restrictions to distinguish between regulated and non-regulated data, zero trust micro-segmentation enables you to establish perimeters around specific categories of sensitive data. Compared to many flat network topologies, micro-segmentation gives better visibility and control during audits or in the event of a data breach.
Gain Access Control
Access control and visibility loss are the two issues that security experts are most concerned about when moving to the cloud. Workload security is still a joint responsibility of your company and the cloud service provider, regardless of improvements in security. In a zero trust, security measures are executed in accordance with the identities of communicating workloads and are directly connected to the workloads.
How Does Zero Trust Work?
Businesses must connect data from all security domains to adopt a zero trust architecture properly. A company’s security teams must concur on priorities and coordinate their access procedures. All connections within the organization, including those between data, users, devices, applications, workloads, and networks, must be secured. A well-planned strategy and roadmap are necessary for incorporating and integrating security tools into this architecture to accomplish certain business-focused objectives.
Conclusion
A zero-trust security model is one of the most significant projects a company can pursue, even if it encounters challenges along the path. However, it requires extensive planning and coordination. So start small, do trials, and then scale up deployments.













