WordPress fixed three safety defects almost a week ago. However, only just recently did the organization address the unknown 0day exploits that allowed unauthorized hackers to edit and alter the content of a page or any article within a WordPress website.
The victim and vulnerabilities at hand exist within the REST API built for WordPress. Two major bugs were found allowing hackers Remote privilege escalation and Content injection.
The major issue at hand here is not the fact that the plugin has bugs in them, every single one out there does, but it’s more to do with the fact that the high-profile Content Management System company is used in millions upon millions of websites and they have made the REST API a default ever since their release of WordPress 4.7.0
The vulnerabilities are simple to manipulate, they affect versions 4.7 and 4.7.1 of the WordPress content management system (CMS), permitting an unauthenticated attacker to change all and any content on unpatched websites and can redirect people to destructive and malicious scripts along with virus infected software’s.
The vulnerabilities in the REST API were found and were reported by Marc-Alexandre Montpas from Sucuri to WordPress’s cyber security department. The security staff at WordPress managed to fix the problems within the API, and then immediately delivered a patch for everyone who has the CMS installed on their websites.
However, no details or factual information were revealed about the vulnerabilities when the patch was deployed to keep hackers from taking advantage of the situation and exploiting websites with the 0day before web administrators around the world could path their WordPress websites.
This is what a core WordPress contributor, Aaron Campbell, had to say about the delay in the disclosure of the bugs:
We believe transparency is in the public’s best interest…[and]… in this case, we intentionally delayed disclosing the issue by one week to ensure the safety of millions of additional WordPress sites.
Data from all four WAFs and WordPress hosts showed no indication that the vulnerability had been exploited in the wild. As a result, we made the decision to delay disclosure of this particular issue to give time for automatic updates to run and ensure as many users as possible were protected before the issue was made public.
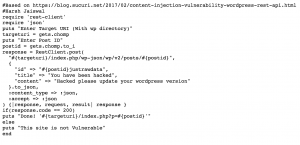
A video created by a user named Harsh Jaiswal demonstrating the Proof of Concept (PoC) of the exploit has been uploaded to YouTube.
The exploit itself has been posted to for any of you who would want to pen-test your WordPress website for the vulnerability and see how the exploit works.
It is advised that for those who have WordPress versions 4.7.0 or 4.7.1 that they download the patches and/or upgrade to the latest updated version of WordPress, version 4.7.2. To get a more in-depth and more detailed clarification concerning the vulnerabilities and exploit, you can go directly to the official post on Sucuri’s blog.